CENTER FOR ADVANCED STUDIES IN SCIENCE AND TECHNOLOGY POLICY [HOME]
EXCERPT: Introduction from Chapter 23
URL: <http://introduction.policy-appliances.info/> (v.061505)
Excerpt from K. A. Taipale, Designing Technical Systems to Support Policy: Enterprise Architecture, Policy Appliances, and Civil Liberties, Chapter 23 in Emergent Information Technologies and Enabling Policies for Counter Terrorism (Robert Popp and John Yen, eds., Wiley-IEEE Press, Jun. 2006) (ISBN:0471776157).
Chapter 23: Designing Technical Systems to Support Policy:
Enterprise Architecture, Policy Appliances, and Civil LibertiesK. A. TAIPALE *
I. Introduction.
It has become cliché to describe the relationship between security and liberty as one requiring the achievement of some optimal balance between two competing and irreconcilable needs. But such cliché is metaphorically misleading. There is no fulcrum point – as is implicit in the balance metaphor – at which point the correct amount of security and liberty can be achieved. Security and liberty are not dichotomous rivals to be traded one for another in a zero sum game as the notion of balance suggests or as the enragés of the public debate would have. Rather, security and liberty are dual obligations of a liberal republic and each must be maximized within the constraints imposed by the other. [1]
The events and subsequent investigations of 9/11 have highlighted the national security need for better information management, and for new technologies and techniques to improve collection, information sharing, and data analysis in counterterrorism applications. The need to manage vast data volumes and better “connect the dots” is uncontroverted and has been explicitly set out in a series of executive orders, presidential directives, national strategy documents, committee reports, and legislation. [2]
However, emergent information technologies that can enable such improved information management and analysis processes – technologies like those described in this book – also challenge traditional policy doctrines and legal structures premised in part on protecting individual liberty by maintaining privacy through the “practical obscurity” arising from inefficiencies in information acquisition, access, management, and analysis. [3] Thus, to some observers, improving the ability of government agencies to “connect the dots” is seen to be in political conflict with the notion of keeping the power to “connect the dots” out of any one hand, particularly that of the central government. [4] The result, as evidenced in the public debate, is a presumed implacable antagonism between security and privacy.
Fortunately, we do not need to resolve this Jacobin discordance in order to design information systems with technical features that can support a broad range of policies to mitigate privacy concerns and still meet security needs. Indeed, there is no inherent technical design conflict at all between security and privacy as the technical features required to support privacy policy are in large part the same technologies required to meet operational information assurance and data security needs in national security or law enforcement information sharing applications. Both national security and privacy policy require (i) that shared information be useful (that is, that data is accurate, reliable, and timely, and that it can be up-dated or corrected as needed), and (ii) that information be used appropriately according to policy rules. Technical features to support these concordant policy needs in information systems include rules-based processing, selective disclosure, data quality assurance, error correction, and strong authorization, logging, and audit functions (to control and record for review and oversight purposes what information goes where, under what constraints, and who has access to it).
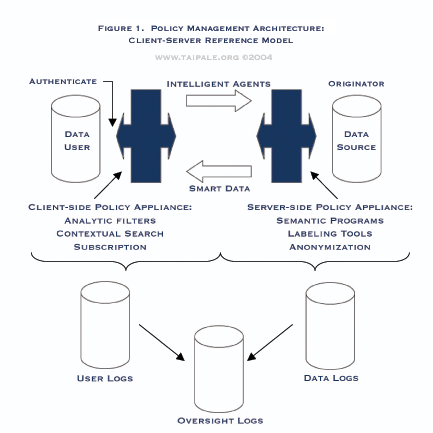
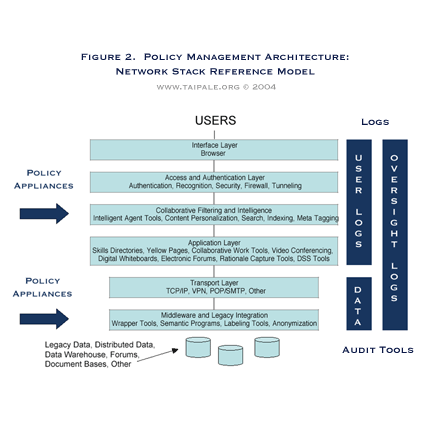
This chapter discusses policy-enabling systems design (see the Policy Appliance Reference Model) based on an enterprise architecture for knowledge management (a lifecycle approach to managing information from production to consumption as a product to support information process needs) that includes policy appliances (technical control mechanisms to enforce policy rules and ensure accountability in information systems) [5], interacting with smart data (data that carries with it contextual relevant terms for its own use) and intelligent agents (queries that are self-credentialed, authenticating, or contextually adaptive). See Figure 1 (Policy Management Architecture: Client-Server Reference Model) and Figure 2 (Policy Management Architecture: Network Reference Model); and the Policy Appliance Reference Model Overview.
It is beyond the scope of this chapter to detail specific technology development or current research avenues in depth, or to exhaustively examine information management strategies or developments. Rather, this chapter provides an overview of the relationship between emerging policy process models and technical design choice in order to better understand the interdependence of technical architecture and policy implementation.
FIGURE 1. POLICY MANAGEMENT ARCHITECTURE: Client-Server Reference Model. An enterprise architecture reference model for knowledge management (an information product approach) that includes policy appliances (technical control mechanisms to enforce policy rules and ensure accountability) interacting with smart data (data that carries with it contextual relevant terms for its own use) and intelligent agents (queries that are self-credentialed, authenticating, or contextually adaptive).
FIGURE 2. POLICY MANAGEMENT ARCHITECTURE: Network Stack Reference Model. An enterprise architecture reference model showing policy appliances (technical control mechanisms to enforce policy rules) and logging functions (to record and audit for accountability) in network layer relationship. This figure builds on the seven-layer knowledge management architecture originally suggested in Amrit Tiwana, The Knowledge Management Toolkit (2000).
* Kim Taipale, BA, JD (New York University), MA, EdM, LLM (Columbia University), is the executive director of the Center for Advanced Studies in Science and Technology Policy. Mr. Taipale is also a senior fellow at the World Policy Institute where he directs the Program on Law Enforcement and National Security in the Information Age and the Global Information Society Project.
[1] K. A. Taipale, Data Mining and Domestic Security: Connecting the Dots to Make Sense of Data, 5 Colum. Sci. & Tech. L. Rev. 2 at n. 6 (2003) [hereinafter, Taipale, Data Mining], citing Thomas Powers, Can We Be Secure and Free? 151 Public Interest 3, 5 (Spring 2003); see also K. A. Taipale, Technology, Security, and Privacy: The Fear of Frankenstein, the Mythology of Privacy, and the Lessons of King Ludd, 7 Yale J. L. & Tech. 123; 9 Intl. J. Comm. L. & Pol'y 8 (2004) [hereinafter, Taipale, Frankenstein].
[2] See, e.g., Executive Order 13356 (2004); Presidential Directive, Strengthening Information Sharing, Access, and Integration B Organizational, Management, and Policy Development Structures for Creating the Terrorism Information Sharing Environment, June 2, 2005; National Strategy for Homeland Security at 55 (2002); The National Commission on Terrorist Attacks Upon the United States, The 9/11 Report §13.3 (2004); Intelligence Reform and Terrorism Prevention Act of 2004, Pub. L. No.108-458, §1016.
[3] See Department of Justice v. Reporters Committee for Freedom of Press, 489 U.S. 749, 780 (1989) (recognizing a legally protected interest in the “practical obscurity” of inefficient paper-based record systems).
[4] See, e.g., Kathleen Sullivan, Under a Watchful Eye: Incursions on Personal Privacy, in The War on Our Freedoms (Richard C. Leone et al., eds., 2003).
[5] See Taipale, Frankenstein, supra note 1 at 56-58 (discussing “privacy appliances” to enforce rules and provide accountability). The concept of privacy appliances originated with the DARPA Total Information Awareness project. See Presentation by Dr. John Poindexter, Director, Information Awareness Office (IAO), DARPA, at DARPA-Tech 2002 Conference, Anaheim, CA (Aug. 2, 2002); ISAT 2002 Study, Security with Privacy (Dec. 13, 2002); and IAO Report to Congress regarding the Terrorism Information Awareness Program at A-13 (May 20, 2003) in response to Consolidated Appropriations Resolution, 2003, No.108-7, Division M, §111(b) [signed Feb. 20, 2003]. See also the Policy Appliance Reference Model Overview <policy-appliances.info/overview/>.
Introduction from K. A. Taipale, Designing Technical Systems to Support Policy: Enterprise Architecture, Policy Appliances, and Civil Liberties, in Emergent Information Technologies and Enabling Policies for Counter Terrorism (Robert Popp and John Yen, eds., Wiley-IEEE Press, Jun. 2006) (ISBN:0471776157). Book is available for purchase from Amazon or Wiley-IEEE Press.
See also, related powerpoint presentation available at <www.counterterrorism-technology.info>
(ABA S. C. L. & Nat. Sec., Nov. 2004).The Policy Appliance Reference Model is a service mark of the Center for Advanced Studies. All material on this page is copyright the Center for Advanced Studies or the editors or publisher referred to above © 2003-2006. Limited permission is granted to reproduce this introduction in whole or in part for non-commercial purposes, provided it is with proper citation and attribution.