CENTER FOR ADVANCED STUDIES IN SCIENCE AND TECHNOLOGY POLICY
Policy Appliance Reference Model Doc. 05-0101-PARM
URL <policy-appliances.info/overview/> (v.060104)Policy Appliance Reference Model: An Overview
K. A. TAIPALE *
The Policy Appliance Reference Model (PARM or the Model) is as a high-level analytic framework around which policy-makers, law-makers, and analysts; information managers, systems architects, and technology developers; the media; and other interested parties including the public can develop a shared understanding of the interdependence of policy development, information management process change, and technical systems design in distributed network systems for information sharing in a variety of applications -- including national security, counter-terrorism, law enforcement, routine government services, health care, ecommerce, corporate, or commercial needs -- throughout the emerging information-based society.
PARM describes an enterprise architecture for information sharing and knowledge management (a lifecycle approach to managing information from production to consumption as a product to support information process needs) based on policy appliances [1] (technical control mechanisms to enforce rules) interacting with smart data (data that carries with it contextual relevant terms for its own use) and intelligent agents (queries that are self-credentialed, authenticating, or contextually adaptive) to reconcile, enforce, and monitor agreed information management policies for information security, data quality, and privacy protection across heterogeneous information sharing systems and networks. The Model supports policy-based information management processes through rules-based processing, selective disclosure, and accountability and oversight.
As is already evident, the emerging global information society will consist of many heterogeneous but interconnected systems that will each be governed or managed according to different policies, rules, or principles that meet local information management needs. (For example, systems may be subject to different international, national or other political subdivision information disclosure or privacy laws; or different information management or security policies among or between government agencies, between government and private sector information systems, or between producers and consumers of proprietary information or intellectual property, etc.)
This interconnected network of systems (for which the Internet as we currently know it serves as the transport layer) will increasingly require dynamic negotiation and agreement of terms through technical mediation to determine which policies will govern information as it flows between or among systems (that is, what use policies will govern what information goes where, under what constraints, and who has access to it for what purposes, etc.).
Because no single policy can govern all systems or information needs, some method of reconciling differences between systems and then enforcing and monitoring agreed policies will have to be devised in order to share useful information across heterogeneous systems with different policies or requirements. Current static methods (and policies) based on all-or-nothing access control are insufficient to meet variable information production and consumption needs, particularly when there are potentially competing policies that are contextually dependent (for example, the conflict between open-government disclosure laws and privacy laws, or between national security needs for data analysis and personal privacy, or between intellectual property protection and fair use, etc.). What is needed are dynamic, contextually-aware control mechanisms – policy appliances – to enforce circumstantially appropriate use policies.
Although policy development is a political or cultural process, not a technological one, technical systems architecture can bound what policy opportunities are ultimately enabled. Thus, some technical means to reconcile, enforce, and monitor policy across systems will be required. In order to maintain the open transport, end-to-end principles embedded in the current Internet design – that is, to avoid hard-coding policy solutions in the transport layer – policy appliances will be required to mediate between systems to facilitate information sharing, data exchange, and management process interoperability.
Policy appliances will increasingly mediate between data owners or producers, data aggregators, and data users, and among heterogeneous institutional systems, networks, or devices, in order to manage information policies and laws across system (or between jurisdictions) with divergent information policies or needs. Policy appliances will interact with smart data (data that carries with it contextual relevant terms for its own use) and intelligent agents (queries that are self-credentialed, authenticating, or contextually adaptive) to control information flows according to appropriate policy, protect security and confidentiality, and maintain privacy.
Policy appliances include technologies that support policy-based information management processes by enabling rules-based processing, selective disclosure, and accountability and oversight:
- rules-based processing technologies include analytic filters, contextual search, semantic programs, labeling and wrapper tools, and DRM, among others;
- selective disclosure technologies include anonymization, encryption, content personalization, subscription and publishing tools, among others; and,
- accountability and oversight technologies include authentication, authorization, immutable and non-repudiable logging, and audit tools, among others.
Control and management oversight of policy appliances will be the key determinants of information use in society, and thus will be subject to ongoing international, national, and individual political, corporate and bureaucratic struggles. Immutable and non-repudiable user, data, and oversight logs subject to transparent but confidential oversight will be necessary to meet accountability and compliance needs for both operational and civil liberties policy. Increasingly, international and national information policy and law will be reliant on technical means of enforcement and accountability through policy appliances and supra-systems authorities. The development, implementation, and control of these mechanisms – as well as the development of the governing policies – must be subject to wide-ranging public discourse, understanding, and ultimately consensus.
(Note that for purposes of the public debate the privacy appliance should be viewed as a metaphor – an analytic mechanism representing the need for policy intervention in technical systems to enforce rules – rather than as any particular technical device or application.)
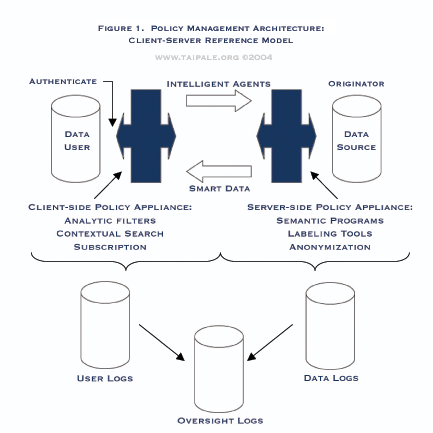
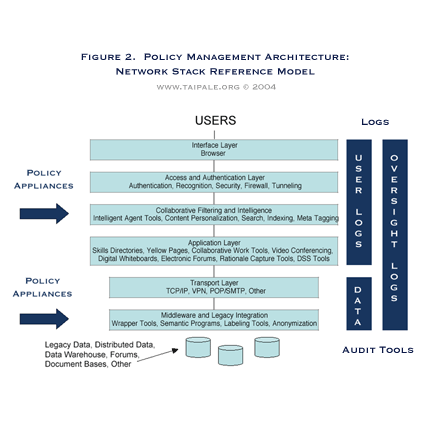
See Figure 1 (Policy Management Architecture: Client-Server Reference Model) and Figure 2 (Policy Management Architecture: Network Reference Model).
FIGURE 1. POLICY MANAGEMENT ARCHITECTURE: Client-Server Reference Model. An enterprise architecture reference model for knowledge management (an information product approach) that includes policy appliances (technical control mechanisms to enforce policy rules and ensure accountability) interacting with smart data (data that carries with it contextual relevant terms for its own use) and intelligent agents (queries that are self-credentialed, authenticating, or contextually adaptive).
FIGURE 2. POLICY MANAGEMENT ARCHITECTURE: Network Stack Reference Model. An enterprise architecture reference model showing policy appliances (technical control mechanisms to enforce policy rules) and logging functions (to record and audit for accountability) in network layer relationship. This figure builds on the seven-layer knowledge management architecture originally suggested in Amrit Tiwana, The Knowledge Management Toolkit (2000).
* Kim Taipale, BA, JD (New York University), MA, EdM, LLM (Columbia University), is the executive director of the Center for Advanced Studies in Science and Technology Policy. Mr. Taipale is also a Senior Fellow at the World Policy Institute where he directs the Program on Law Enforcement and National Security in the Information Age and the Global Information Society Project.
[1] Policy appliances are described in K. A. Taipale, Designing Technical Systems to Support Policy: Enterprise Architecture, Policy Appliances, and Civil Liberties, in Emergent Information Technologies and Enabling Policies for Counter Terrorism (Robert Popp and John Yen, eds., Wiley - IEEE Press, 2006) (ISBN:0471776157). Book is available for purchase from Amazon or Wiley-IEEE Press. See also K. A. Taipale, Technology, Security, and Privacy: The Fear of Frankenstein, the Mythology of Privacy, and the Lessons of King Ludd, 7 Yale J. L. & Tech. 123; 9 Intl. J. Comm. L. & Pol'y 8 (2004) at 56-58 (discussing “privacy appliances” to enforce rules and provide accountability). The concept of privacy appliances originated with the DARPA Total Information Awareness project. See Presentation by Dr. John Poindexter, Director, Information Awareness Office (IAO), DARPA, at DARPA-Tech 2002 Conference, Anaheim, CA (Aug. 2, 2002); ISAT 2002 Study, Security with Privacy (Dec. 13, 2002); and IAO Report to Congress regarding the Terrorism Information Awareness Program at A-13 (May 20, 2003) in response to Consolidated Appropriations Resolution, 2003, No.108-7, Division M, §111(b) [signed Feb. 20, 2003].
See also, related powerpoint presentation available at <www.counterterrorism-technology.info>
(ABA S. C. L. & Nat. Sec., Nov. 2004).The Policy Appliance Reference Model is a service mark of the Center for Advanced Studies. All material on this page is copyright the Center for Advanced Studies © 2003-2005. Permission is granted to reproduce in whole or in part for non-commercial purposes, provided it is with proper citation and attribution.